As more and more companies move their applications to the cloud, ensuring that their data and systems are secure has become increasingly important. However, with the myriad of options available in cloud computing, it can be challenging to know where to start when it comes to securing your cloud-based assets.
In this blog, we will answer some of the most common cloud security concerns, including how to secure your cloud data, what kinds of security measures to implement in the cloud, and how to ensure compliance with regulations. By the end of this blog, you will better understand how to protect your organization’s cloud infrastructure from potential security threats.
Cloud security refers to the rules and procedures used to protect cloud-based applications, data, and infrastructure from unauthorized access. It varies from domain to domain, and few standard security measures are taken care of by cloud service providers. There are various types of cloud security measures that we need to follow while adopting a cloud platform. The most well-known service providers, including Microsoft Azure, Amazon Web Services (AWS), and Google Cloud Platform (GCP), advise a standard protocol.
Here are the answers to some of the most common cloud security concerns:
What are the considerations for selecting a cloud security provider?
Critical considerations for selecting a cloud security provider include evaluating their security features and capabilities, assessing their compliance with relevant regulations and industry standards, reviewing their track record and reputation, and evaluating their ability to provide responsive and effective support.
How can organizations ensure compliance with relevant regulations and industry standards in the cloud?
Organizations can ensure compliance with relevant regulations and industry standards in the cloud by selecting a cloud service provider that complies with these standards and regulations. Additionally, they can implement robust security controls and monitoring mechanisms and perform regular audits and assessments to identify and remediate any compliance gaps.
What is the shared responsibility model for cloud security?
The shared responsibility model for cloud security refers to the division of security responsibilities between the cloud service provider and the customer. The cloud service provider (CSP) is responsible for securing the infrastructure, while the customer is responsible for securing the data and applications they store and use in the cloud.
How can we ensure data is secure in the cloud, and what services are available over the most popular cloud service providers?
One cloud security concerns is how to secure data in cloud, to ensure data is secure in the cloud, we should choose a reputable cloud service provider with strong security measures in place, encrypt our data both in transit and at rest, use strong passwords and multi-factor authentication, regularly monitor activity logs, and implement appropriate access controls. Data security refers to protecting the data stored and processed in the cloud. It involves measures such as encryption, access control, and backup and recovery.
Azure, AWS, and GCP provide a range of data protection tools and services to help organizations secure their cloud data. Here are some examples of data protection tools for each platform:
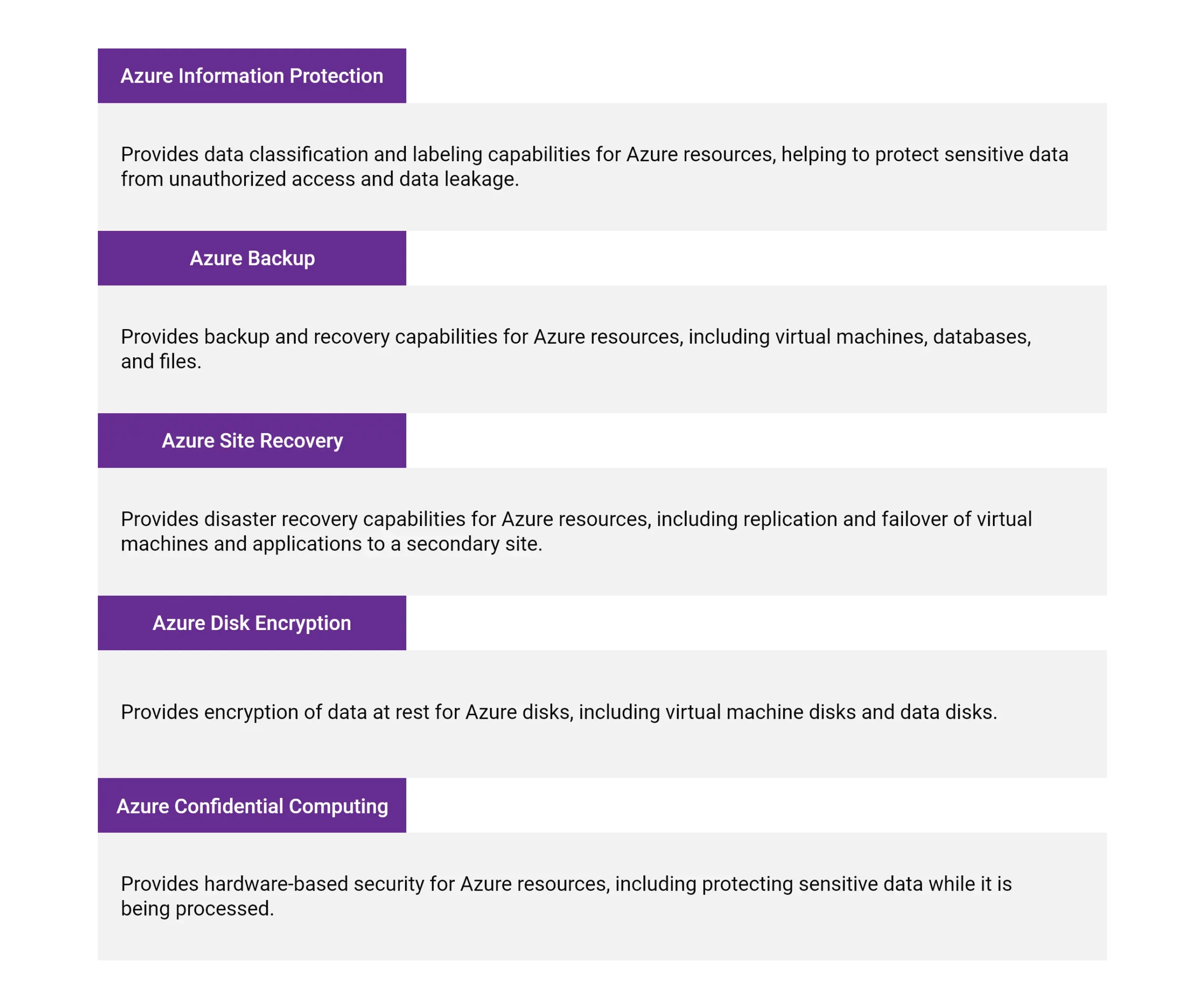
For Azure
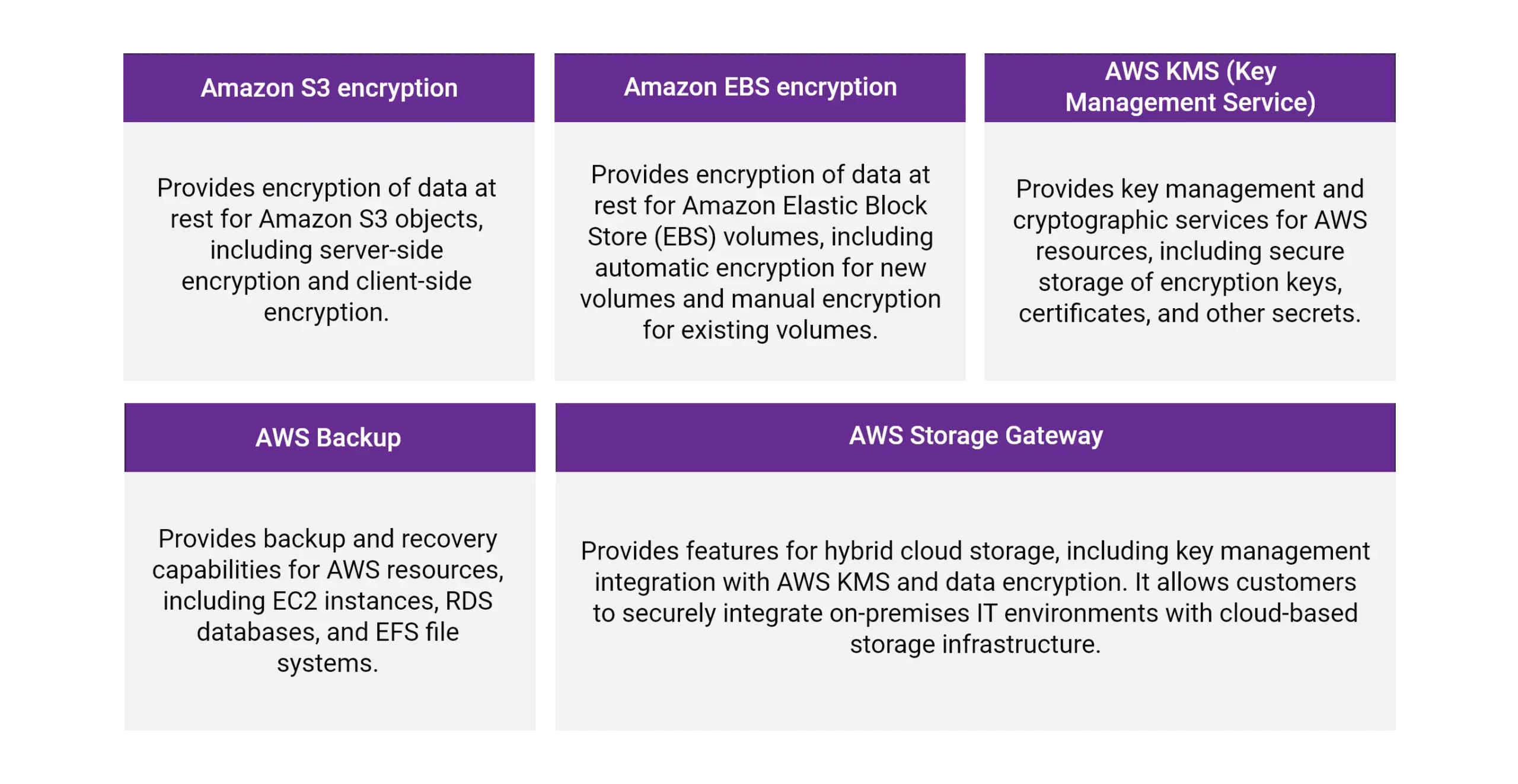
For AWS
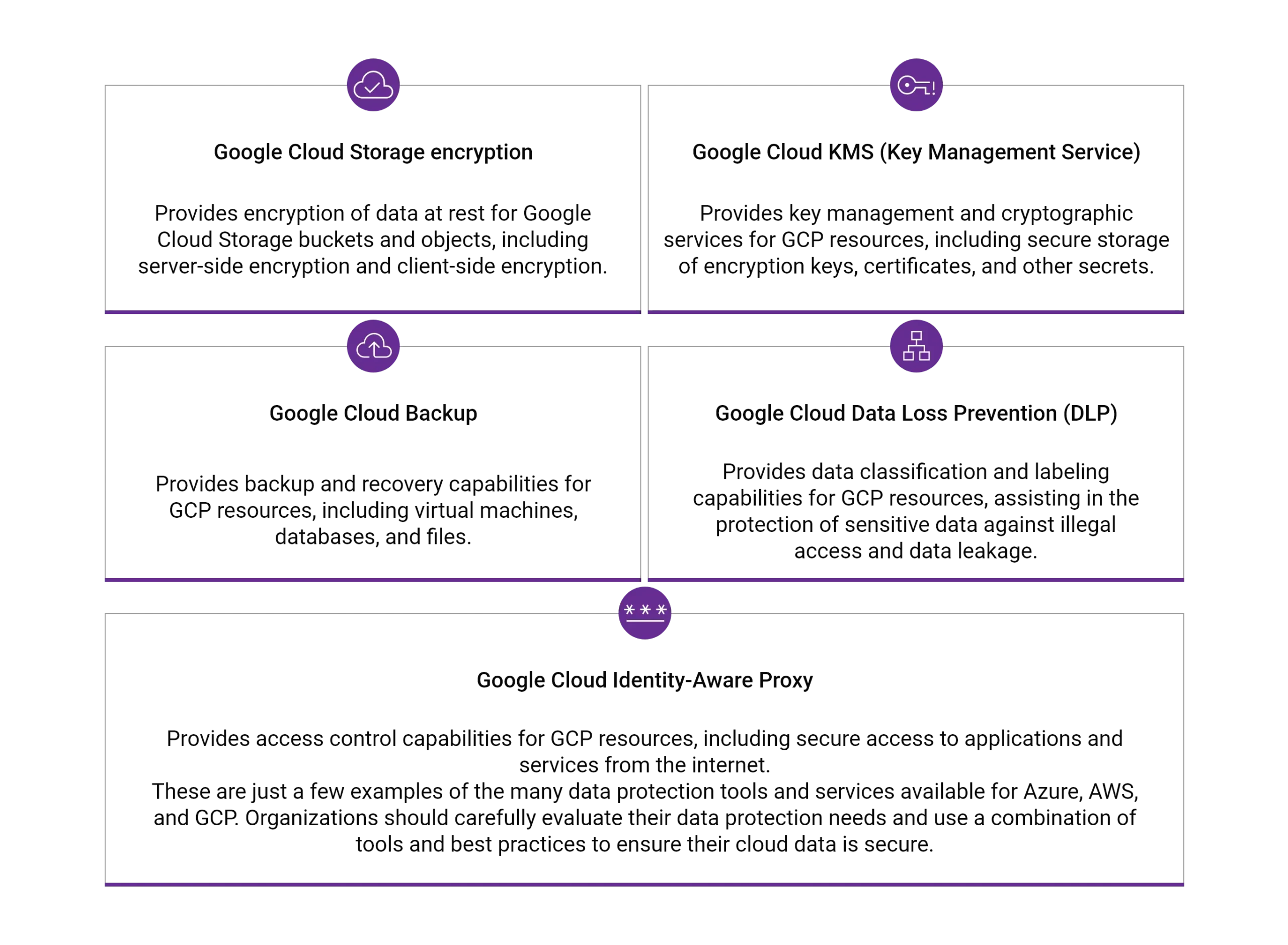
For GCP
What are some cloud security certifications with compliance frameworks?
When choosing a cloud service provider, look for Cloud security certifications that meet rigorous security standards and have undergone regular security assessments. Most commonly, Azure, AWS, and GCP provide the same certifications like:
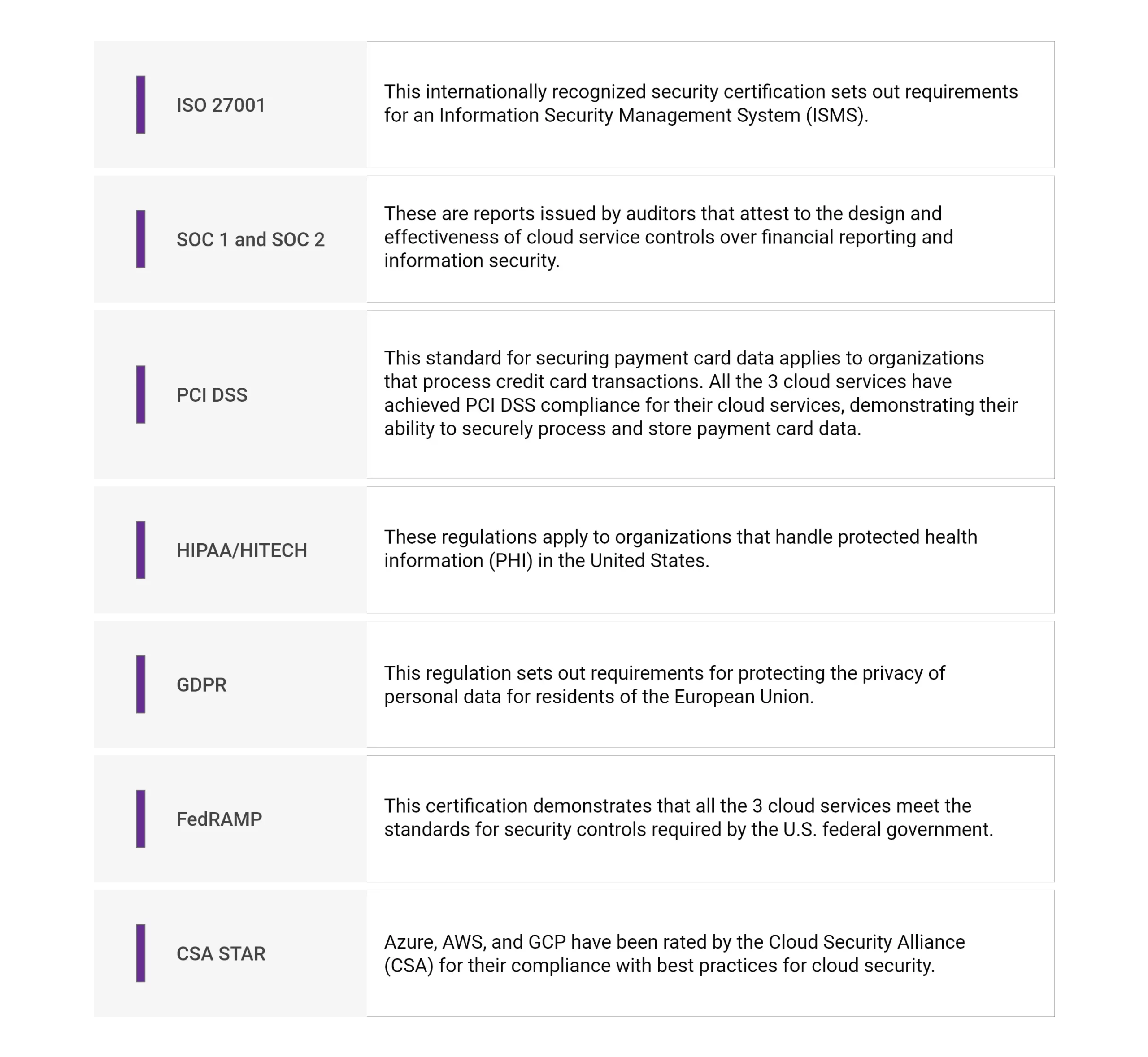
These certifications assure organizations that all the 3 cloud service providers have implemented strong security controls and meet industry standards for security and compliance. Organizations should ensure that their own security and compliance requirements align with these certifications before selecting their cloud provider.
What is Network Security?
Network security is the practice of securing computer networks from unauthorized access, data theft, and other malicious activities. It involves implementing various technologies and processes to prevent and detect unauthorized access, misuse, modification, or denial of computer network and network-accessible resources.
Examples of network security tools include firewalls, intrusion detection and prevention systems, and virtual private networks (VPNs). These precautions aid in defending cloud-based networks against online dangers like malware, phishing scams, and distributed denial of service (DDoS) attacks.
How can we define application security over the cloud?
This refers to protecting the applications hosted in the cloud and involves measures such as secure coding practices, vulnerability testing, and access control.
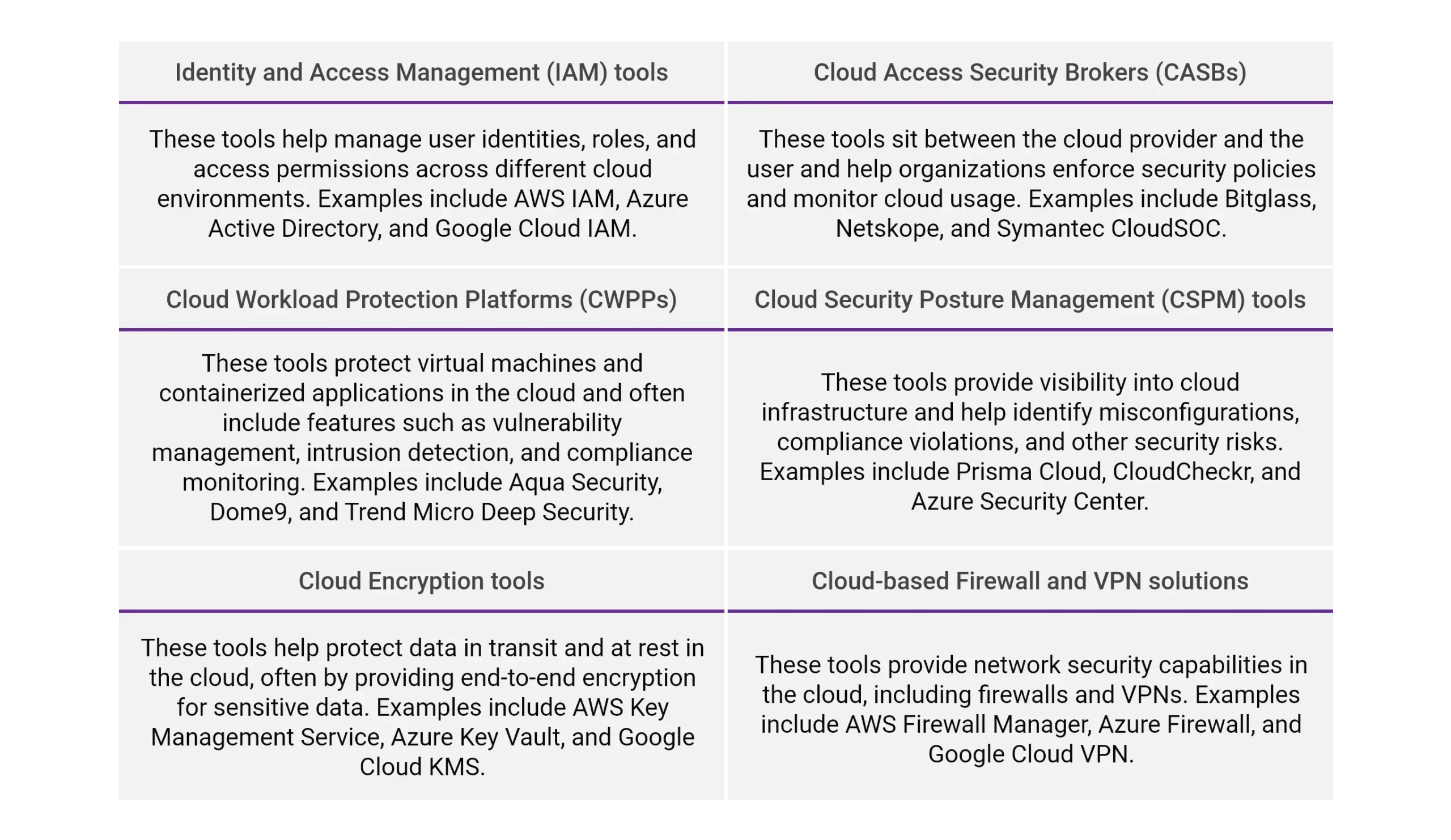
What are the cloud security tools available?
Many tools are available for cloud security. The best tools for particular needs will depend on multiple factors, such as the type of cloud infrastructure we use, the level of security we require, and our budget. Here are some popular tools & technologies for cloud security:
What are some commonly prevalent cloud attacks?
Cloud attacks are one among the other common cloud security concerns. As cloud computing continues to become more prevalent, cybercriminals are increasingly targeting cloud environments with a variety of attacks. Here are some of the latest types of attacks on the cloud:
Data breaches
As attackers try to access sensitive data housed in the cloud, data breaches continue to pose a serious danger to cloud security. This can be accomplished through various methods, including exploiting vulnerabilities in cloud applications, using stolen credentials, or leveraging misconfigured permissions.
Denial of Service (DoS) attacks
DoS attacks attempt to overload a cloud system with traffic, making it unavailable to users. These attacks can be launched from various sources, including botnets or hacked cloud instances.
Advanced Persistent Threats (APTs)
APTs are sophisticated attacks that target specific cloud environments, often with the goal of stealing sensitive data or disrupting operations. These attacks are tough to detect and can go undetected for long periods.
Man-in-the-middle (MitM) attacks
MitM attacks involve intercepting and manipulating data as it flows between cloud systems and users. Attackers may use this to steal sensitive data or inject malware into cloud environments.
Supply chain attacks
Supply chain attacks target third-party providers of cloud services, such as software vendors or cloud infrastructure providers. These attacks can compromise the security of entire cloud environments, potentially exposing sensitive data and disrupting operations.
Crypto-jacking
Crypto-jacking involves hijacking a cloud instance’s computing resources to mine cryptocurrency, often without the owner’s knowledge or consent. This can lead to increased costs for the cloud user and reduced performance for legitimate applications running on the instance.
Container and API attacks
Attackers often target containerized applications and APIs due to their critical role in cloud environments. Attackers may exploit vulnerabilities in container images or APIs to gain access to cloud resources.
What are some enhanced cloud security tools designed by popular service providers?
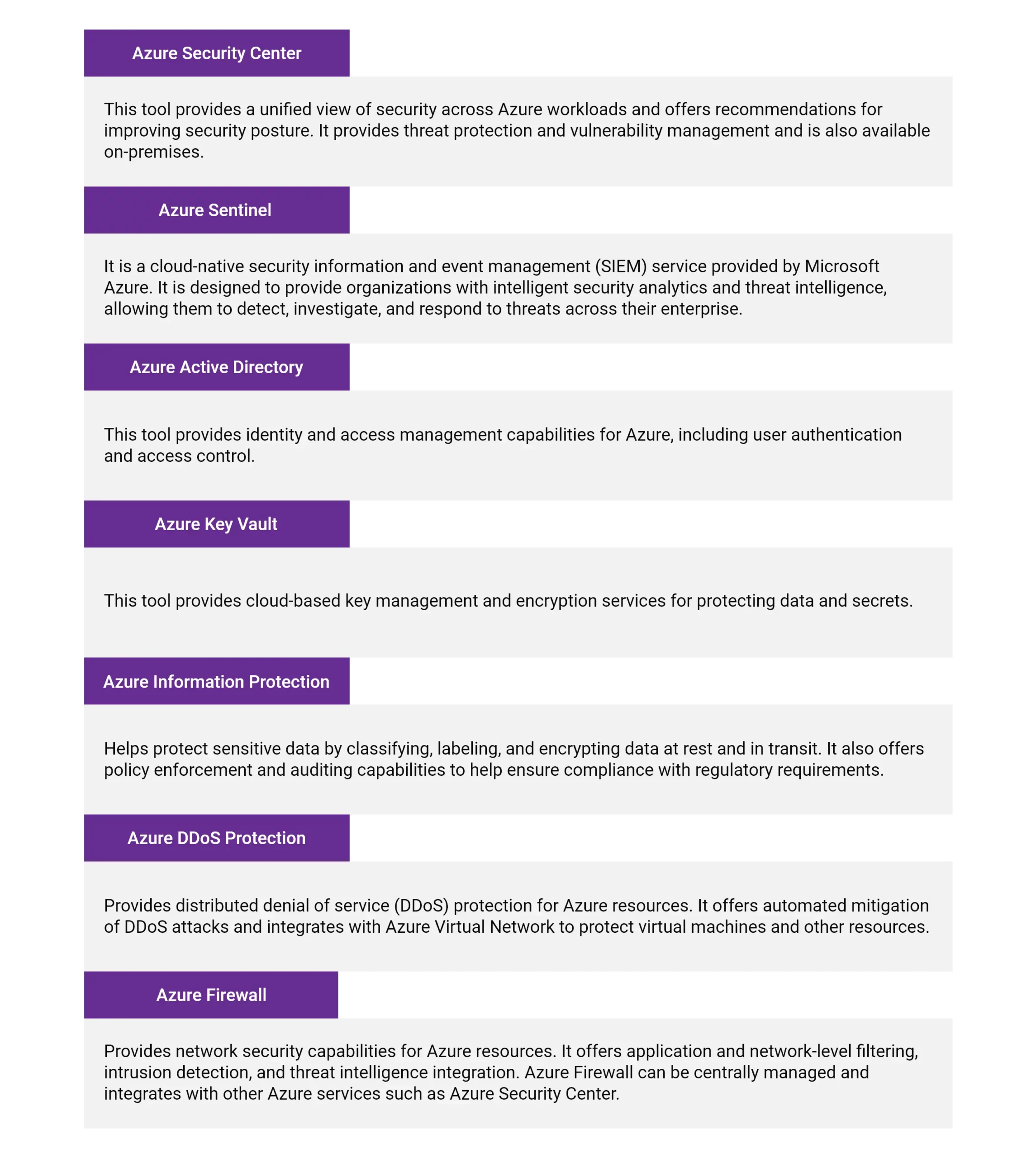
Here are some popular tools for cloud security that are designed by Azure, AWS, and Google Cloud:
For Azure
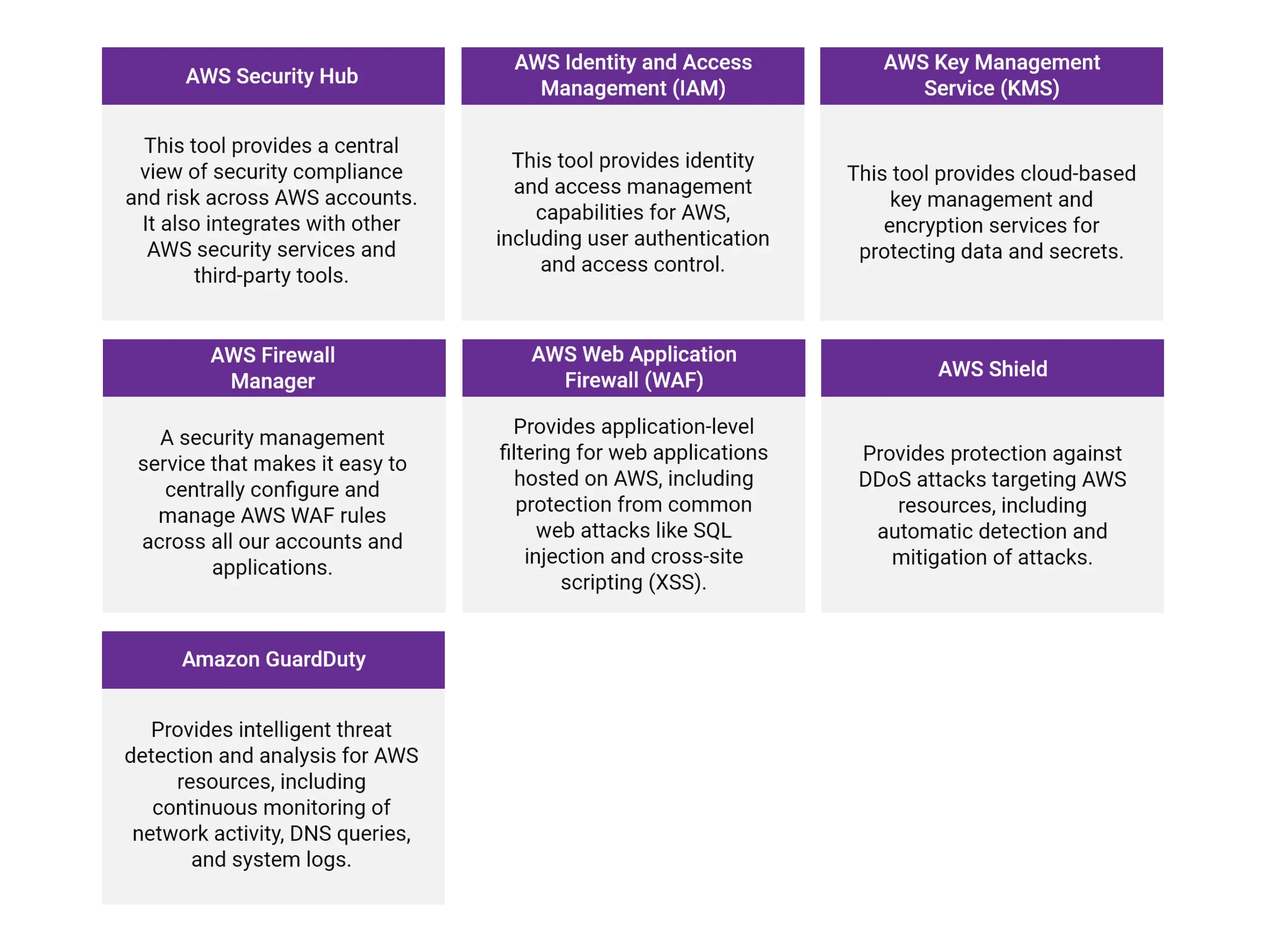
For AWS
For Google Cloud:
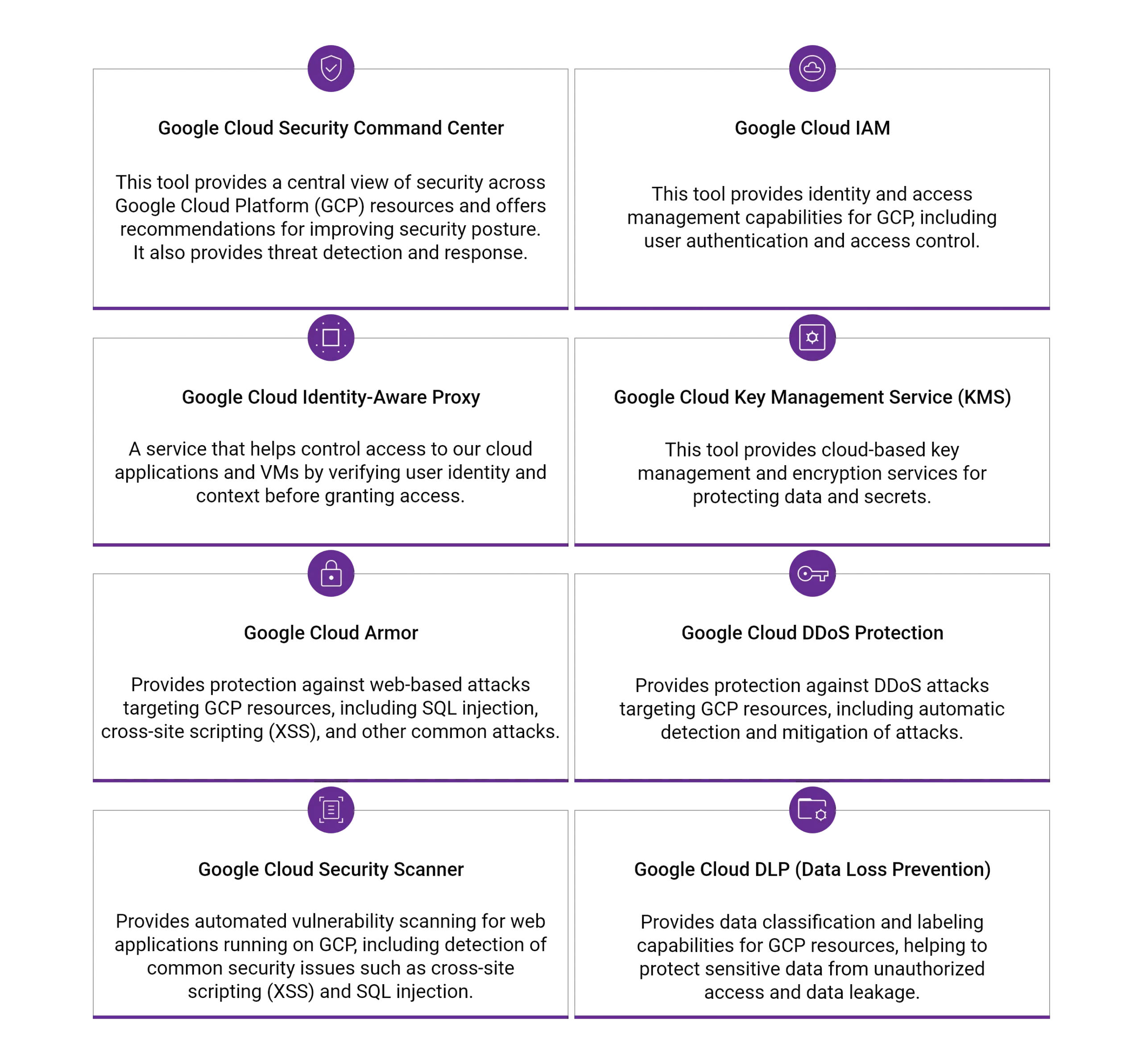
Conclusion
In conclusion, cloud security is paramount for organizations that store their data and run their operations in the cloud. It’s important to understand that the ones listed in this blog are just a few examples of the many tools available for cloud security in Azure, AWS, and Google Cloud. The optimal tool for our specific needs will rely on several variables, including our budget, the size and complexity of our cloud environment, and our unique security requirements.
As discussed in this blog, securing cloud-based assets requires implementing robust security measures, such as encryption, access controls, and monitoring, as well as ensuring compliance with relevant regulations. Organizations can protect their data, applications, and systems from potential security breaches and maintain their customers’ trust by taking these steps.As cloud computing grows, staying vigilant and proactive about cloud security is essential to ensure your organization stays ahead of potential threats.
Ultimately, cloud security is all about ensuring the confidentiality, integrity, and availability of cloud-based resources and data while minimizing the risks associated with cloud computing.