We’ve advanced well into the age of modern technology, primarily regarding business operations and the digital modernization of daily workflows and processes. The importance of securing a company against cybersecurity-related threats and hazards is impossible to ignore.
Security breaches are astoundingly costly, adding up to millions in damages for many companies annually. When caught unprepared, security problems can wreak havoc on your organization.
Security architecture boosts encryption and reduces the risk of cyber-attacks, and protects your company and consumer assets and data from harm. We’ll start with an overview of security architecture and what it means for your business to establish a strong foundation of security management.
Understanding Security Architecture
Security architecture has many different meanings and definitions for various companies. Ultimately, the security architecture is a set of established security principles and methods that align with your company objectives and keeps your sensitive information safe from potential cyber threats and attacks.
Security architects examine the current status of your business regarding security, and then they’ll produce a blueprint, or a plan, to help you achieve your desired security outcome. A security architect will guide your teams, helping you establish security management and rules and regulations to keep your data safe from every angle.
The Purpose of Security Architecture
The purpose behind security architecture is to protect your organization from outside threats. To meet this goal, security architects will often insert themselves within your daily business practices to learn as much as possible about you, your company, and the people who work for you.
They’ll have conversations with your employees, team leaders, and management to seek an understanding of your business goals, what your systems require from a security perspective, the needs of your customer base, and other critical factors.
Once they’ve gathered all the necessary information, they can construct a plan and offer guidance that suits your business objectives and cyber risk. An expert security architect will help you find the perfect balance between security and complexity, securing your systems and data without enforcing over-the-top security measures that might interfere with your current processes.
Secret Architecture: The Other Side of Security Architecture
If you’ve got a good and effective security architecture in place, the chances are that everyone in your company is a part of that architecture. From routinely creating new log-in passwords to sending secure emails, your employees know the deal regarding security and the responsibility they have surrounding it.
However, even by a skilled professional, building a security architecture doesn’t always involve secret architecture, which has become notoriously challenging to manage. Managing secrets, or sensitive entities such as passwords and API keys, continues to prove troublesome for security teams.
Many developers continue to store plaintext passwords inside a collaborative platform like GitLab or keep sensitive credentials inside Docker images that anyone can access. It’s crucial to find a somewhat simple solution to preventing outside leaks, especially when talking about the ability of software to deliver while remaining reliable.
Of course, access to secrets like passwords is typically restricted, but companies must consider which route to take in various situations concerning secret architecture. For example, what happens when the employee leaves? Many angles require examination from external parties with access to security breaches when discussing secret architecture.
Performing a monthly audit to determine who accessed company secrets, establishing different levels of access groups, and understanding how different cloud platforms access different applications are essential components of understanding the path your business should take in security and secret architecture. Of course, secret architecture will not be the same from company to company, but asking yourself the right questions creates a fantastic starting point.
Building Your Secret Architecture
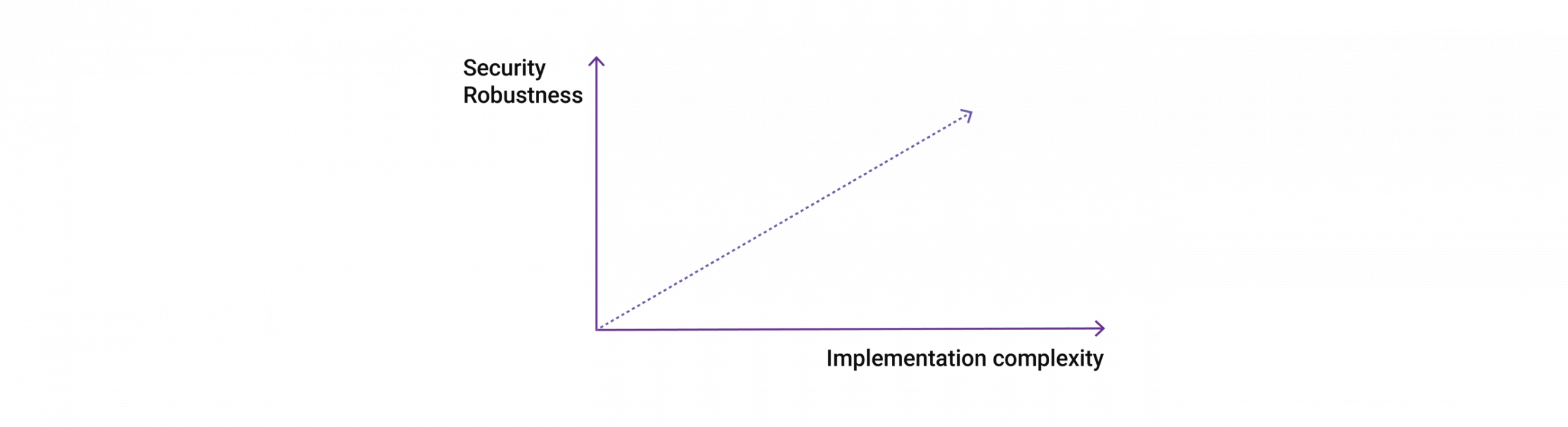
There are various technologies that businesses can combine to find a solution that makes sense through the balance of security and complexity levels. Many tools labeled “too complex” are often misunderstood.
Still, it’s crucial that companies and business leaders understand that specific tools should be used only when it’s beneficial to the project in question. The stronger a security solution, the more complexities it could add to your development process.
Define Your Project Goals
Developing a secret architecture for your business and DevOps processes is nothing other than a modern tech journey. Before establishing security or secret architecture, you must maintain open, honest communication with your team members.
Talk to them privately or in a group setting (whatever works best for your business and team dynamic) about the following:

Your team members should state the current status, any concerns, priorities, and expected timelines regarding each of the talking points mentioned above. Access to this essential inside information will help you define the fundamental (if not more complex) features of the secret architecture you want to implement.
It’s not advised to introduce complicated secret management solutions immediately. Because security measures must be a company-wide effort, especially in DevSecOps, you must ensure everyone is on board.
Begin by allowing your teams to become comfortable with new technology, keeping the lines of communication wide open. As time passes, you can evolve the difficulty level of new software and technologies, increasing the sophistication of your secret architecture process.
Gradually Adding Complexity
It helps to think of your secret architecture as three steps concerning the addition of complex measures your team will eventually have to take. When you map out the levels of complexity for them, you can spark discussion among the team and assist them in visualizing how secret management architecture will look and evolve.

Secret Architecture Technology
Now that we’ve mapped out your potential plan for putting your secret architecture into place, you’ll want to understand a few technologies you can utilize to get the job done. They needn’t be used all at once, and you may find that some will serve you better than others.
Git-Crypt
Git-Crypt encrypts files in a git repository. It’s an open-source project that relies on git hooks and requires the knowledge of a professional to execute. Any file listed with .gitattributes will automatically encrypt before it goes to the repository for storage. Decrypting these files is not easy, and as a whole, Git-Crypt comes with inevitable conflicts that your secret architect can help you address.
AWS Key Management Service
Hosted by AWS, encryption key management can encrypt an encryption key. Once you’ve encrypted the original key, it is ineffective in decrypting any of your secrets, which means it’s safe to store your encrypted version along with your other secrets.
You can choose to discard or store the original encryption key as long as you have access to a safe and reliable backup. AWS has it handled and can decrypt your encrypted encryption key.
ChefVault
ChefVault is a somewhat complex provisioning tool that allows users to describe everything from registered users to installed applications. ChefVault stores your descriptions in their “recipe” system, which you can contain in their “cookbooks.”
Secrets tend to be necessary to complete various tasks during a provisioning process, such as needing password access for a new database installation or onboarding aspects like creating new users. ChefVault makes it possible to obtain these secrets without jumping through (too many) hoops.
The Perfect Balance Between Security and Complexity
The secret to finding the perfect balance between security and complexity lies in knowing how many layers of protection your company needs and which technology can help you execute those layers. Open communication and a slow secret architecture implementation will keep your team from becoming overwhelmed, allowing you to establish the security you need without confusion. When you keep the process slow and steady, you prevent it from becoming too complicated.